Here you will find answers to EIGRP Questions
Note: If you are not sure about EIGRP, please read my EIGRP tutorial
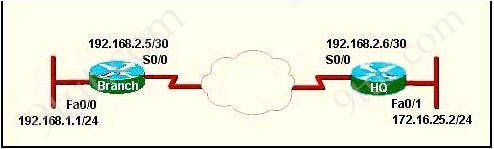
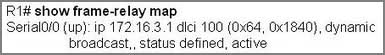
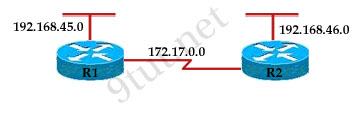
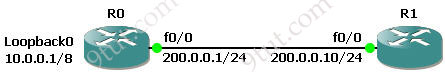
Question 1
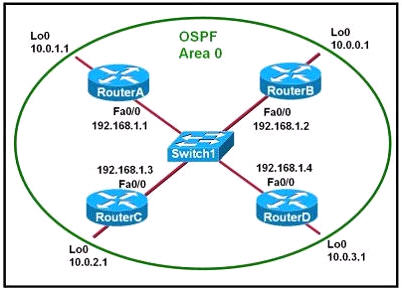
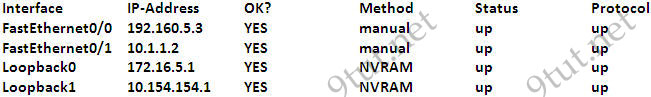
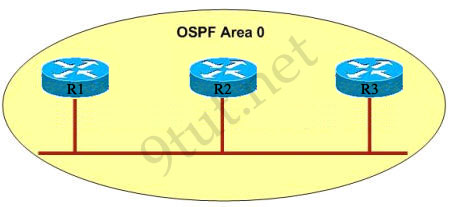
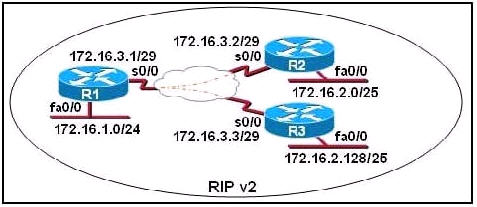
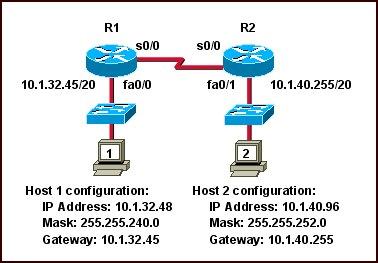
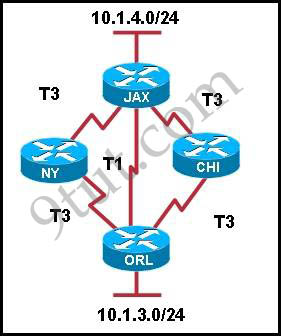
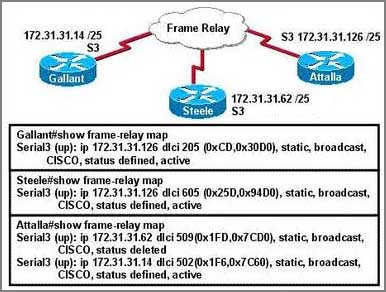
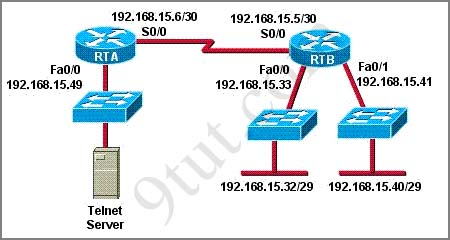
Refer to the exhibit, when running EIGRP what is required for R1 to exchange routing updates with R3?
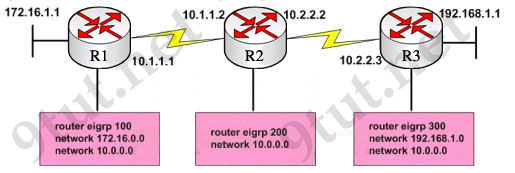
A – AS numbers must be changed to match on all the routers
B – Loopback interfaces must be configured so a DR is elected
C – The no auto-summary command is needed on R1 and R3
D – R2 needs to have two network statements, one for each connected network
Answer: A
Question 2:
As a Cisco technician, you need to know EIGRP protocol very well. Which of the following is true about EIGRP successor routes? (Choose two)
A – A successor route is used by EIGRP to forward traffic to a destination
B – Successor routes are stored in the neighbor table following the discovery process
C – Successor routes are flagged as “active” in the routing table
D – A successor route may be backed up by a feasible successor route
E – Successor routes are stored in the neighbor table following the discovery process.
Answer: A D
Explanation:
B is not correct because neighbor table only contains a list of directly connected EIGRP routers that have an adjacency with this router, it doesn’t contain successor routes.
C is not correct because successor routes are not flagged as “active”, they are always the best route to reach remote networks and are always used to send packets.
A and D are correct because successor route is the best and primary route to a remote network. It is stored in the routing table and topology table. If this route fails, a backup route (called feasible successor route) in the topology table will be used to route traffic to a destination.
Question 3:
Which two statements are true regarding EIGRP? (Choose two)
A – Passive routes are in the process of being calculated by DUAL
B – EIGRP supports VLSM, route summarization, and routing update authentication
C – EIGRP exchanges full routing table information with neighboring routers with every update
D – If the feasible successor has a higher advertised distance than the successor route, it becomes the primary route
E – A query process is used to discover a replacement for a failed route if a feasible successor is not identified from the current routing information
Answer: B E
Explanation:
Diffusing Update Algorithm (DUAL) is the algorithm for selecting and maintaining the best path to each remote network. DUAL tracks all the routes advertised by neighbors and selects routes based on feasible successors. It inserts lowest cost paths into the routing table (these routes are known as primary routes or successor routes) -> A is not correct.
EIGRP is still a distance-vector protocol, but has certain features that belong to link-state algorithms (like OSPF) than distance-vector algorithms. For example, EIGRP sends a partial routing table update, which includes just routes that have been changed, not the full routing table like distance-vector algorithms -> C is not correct.
The feasible successor route will become the primary route when its advertised distance is lower than the feasible distance of the successor route. The feasible successor route can be used in the event that the successor route goes down. Notice that the feasible successor route does not get installed in the routing table but is kept in the topology table as a backup route -> D is not correct.
“Support VLSM, route summarization, and routing update authentication” are the features of EIGRP -> B is correct.
When a route fails and has no feasible successor, EIGRP uses a distributed algorithm called Diffusing Update Algorithm (DUAL) to discover a replacement for a failed route. When a new route is found, DUAL adds it to the routing table -> E is correct.
Question 4
Which type of EIGRP route entry describes a feasible successor?
A. a primary route,stored in the routing table
B. a backup route,stored in the routing table
C. a backup route,stored in the topology table
D. a primary route,stored in the topology table
Answer: C
Explanation
Feasible successor is a route whose Advertised Distance is less than the Feasible Distance of the current best path. A feasible successor is a backup route, which is not stored in the routing table but stored in the topology table.
Question 5
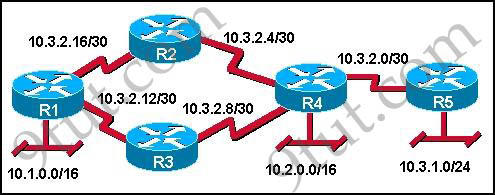
Refer to the exhibit. Given the output from the show ip eigrp topology command, which router is the feasible successor?
| router# show ip eigrp topology 10.0.0.5 255.255.255.255 IP-EIGRP topology entry for 10.0.0.5/32 State is Passive, Query origin flag is 1, 1 Successor(s), FD is 41152000 |
A.
| 10.1.0.1 (Serial0), from 10.1.0.1, Send flag is 0×0 Composite metric is (46152000/41640000), Route is Internal Vector metric: Minimum bandwidth is 64 Kbit Total delay is 45000 Microseconds Reliability is 255/255 Load is 1/255 Minimum MTU is 1500 Hop count is 2 |
B.
| 10.0.0.2 (Serial0.1), from 10.0.0.2, Send flag is 0×0 Composite metric is (53973248/128256), Route is Internal Vector Metric: Minimum bandwidth is 48 Kbit Total delay is 25000 Microseconds Reliability is 255/255 Load is 1/255 Minimum MTU is 1500 Hop count is 1 |
C.
| 10.1.0.3 (Serial0), from 10.1.0.3, Send flag is 0×0 Composite metric is (46866176/46354176), Route is Internal Vector metric: Minimum bandwidth is 56 Kbit Total delay is 45000 microseconds Reliability is 255/255 Load is 1/255 Minimum MTU is 1500 Hop count is 2 |
D.
| 10.1.1.1 (Serial0.1), from 10.1.1.1, Send flag is 0×0 Composite metric is (46763776/46251776), Route is External Vector metric: Minimum bandwidth is 56 Kbit Total delay is 41000 microseconds Reliability is 255/255 Load is 1/255 Minimum MTU is 1500 Hop count is 2 |
Answer: B
Explanation
To be the feasible successor, the Advertised Distance (AD) of that route must be less than the Feasible Distance (FD) of the successor. From the output of the “show ip eigrp topology 10.0.0.5 255.255.255.255″ we learn that the FD of the successor is 41152000.
Now we will mention about the answers, in the “Composite metric is (…/…)” statement the first parameter is the FD while the second parameter is the AD of that route. So we need to find out which route has the second parameter (AD) less than 41152000 -> only answer B satisfies this requirement with an AD of 128256.
Question 6
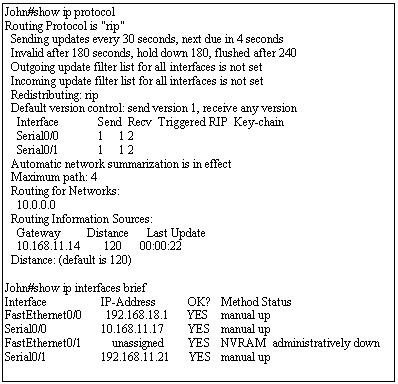
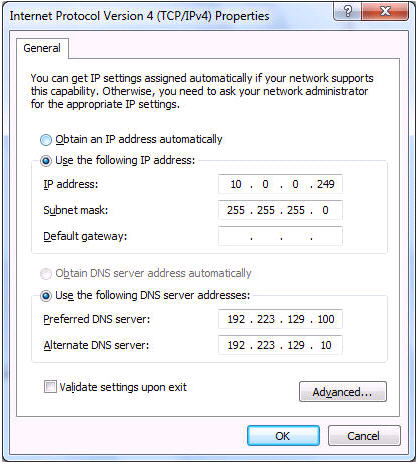
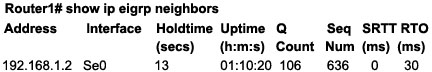
A network administrator is troubleshooting an EIGRP problem on a router and needs to confirm the IP addresses of the devices with which the router has established adjacency. The retransmit interval and the queue counts for the adjacent routers also need to be checked. What command will display the required information?
A. Router# show ip eigrp adjacency
B. Router# show ip eigrp topology
C. Router#show ip eigrp interfaces
D. Router#show ip eigrp neighbors
Answer: D
Explanation
Below is an example of the show ip eigrp neighbors command. The retransmit interval (Smooth Round Trip Timer – SRTT) and the queue counts (Q count, which shows the number of queued EIGRP packets) for the adjacent routers are listed:
Question 7
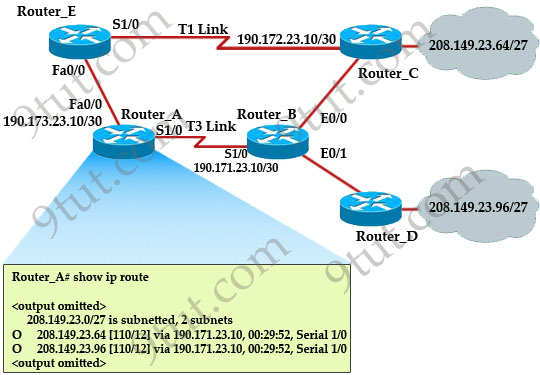
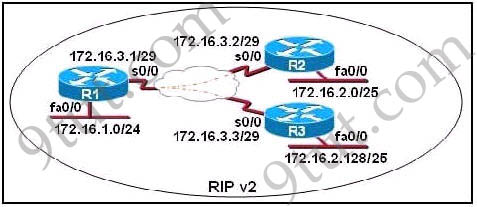
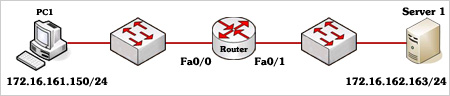
Refer to the exhibit. How many paths can the EIGRP routing process use to forward packets from HQ_Router to a neighbor router?
| HQ_Router# show ip protocols Routing Protocol is “eigrp 109″ Outgoing update filter list for all interfaces is not set Incoming update filter list for all interfaces is not set Default networks flagged in outgoing updates Default networks accepted from incoming updates EIGRP metric weight K1=1, K2=0, K3=1, K4=0, K5=0 EIGRP maximum hopcount 100 EIGRP maximum metric variance 3 Redistributing: eigrp 109 EIGRP NSF-aware route hold timer is 240s Automatic network summarization is not in effect Maximum path: 4 Routing for Networks: 20.10.10.0/24 172.30.10.0/24 192.168.1.0 Routing Information Sources: Gateway Distance Last Update 20.10.10.2 90 00:13:12 172.30.10.2 90 01:13:06 Distance: internal 90 external 170 HQ_Router# |
A. two equal-cost paths
B. two unequal-cost paths
C. three equal-cost paths
D. three unequal-cost paths
E. four equal-cost paths
F. four unequal-cost paths
Answer: F
Explanation
The “Maximum path: 4″ means EIGRP can use up to 4 equal-cost paths to forward packets from HQ_Router to a neighbor router. But here the variance is set to 3 which allows unequal-cost paths. Therefore in this case EIGRP can use up to four unequal-cost paths.
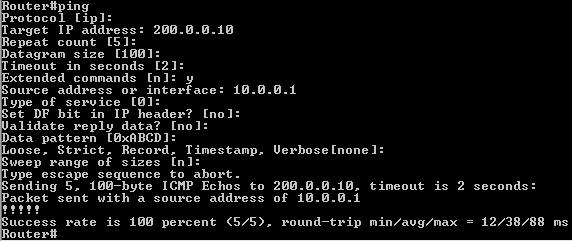
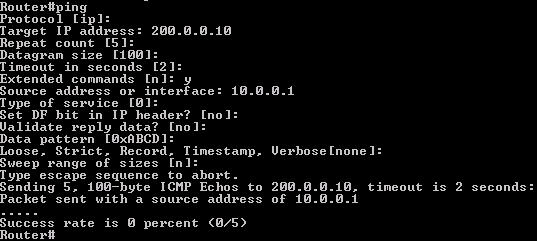
Question 8
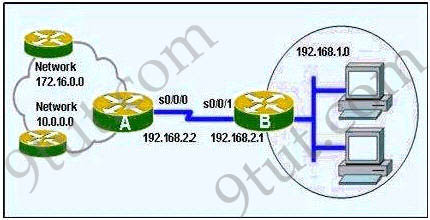
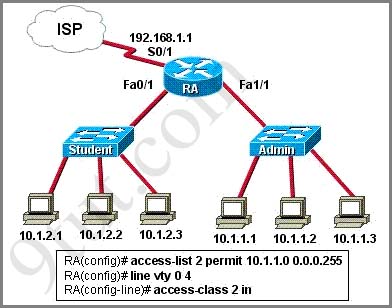
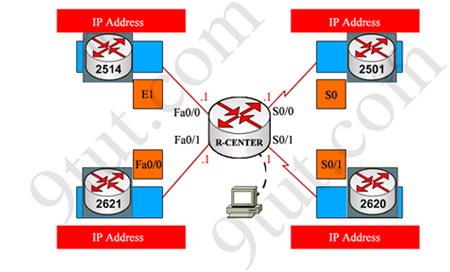
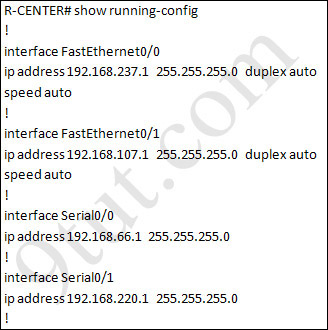
IP address and routing for the network are configured as shown in the exhibit. The network administrator issues the show ip eigrp neighbors command from Router1 and receives the output shown below the topology. Which statement is true?
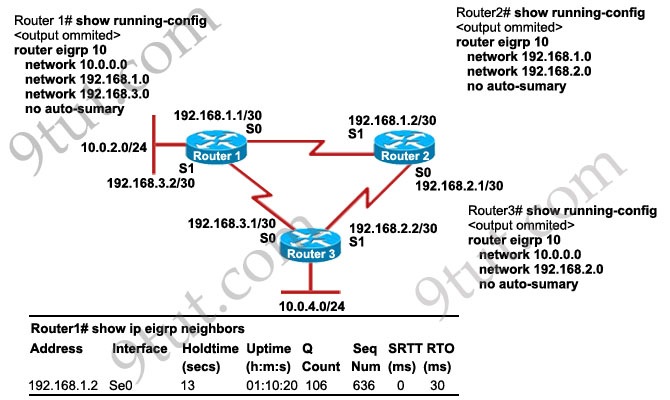
A. It is normal for Router1 to show one active neighbor at a time to prevent routing loops.
B. Routing is not completely configured on Router3.
C. The IP addresses are not configured properly on the Router1 and Router3 interfaces.
D. The no auto-summary command configured on the routers prevents Router1 and Router2 from forming a neighbor relationship.
Answer: B
Explanation
From the output of Router1, we learn that Router1 has not established neighborship with R3 yet. Also from the “show running-config” on Router3 we notice that the “network 192.168.3.0″ statement is missing -> the configuration on Router3 is not complete.